Access rules for users and groups
To give an SSO user access to a repository, you will map that user (or
an SSO group that they belong to) to a database
account. These mappings are provided by
access rules in Cyral. Each access rule is an identity mapping of
an SSO user or group to a database account. For example, SSO user
Frank Hardy might map to a local account — a PostgreSQL user —
called analyst.
Access rules also allow you to specify conditions for and limits on users' repository connections. These can include:
- a start and end time that specify when the access rule is valid;
- requiring the user to complete multi-factor (MFA) token authentication; and/or
- limiting access to the hours when the employee is on-call.
info
Cyral also offers just-in-time approvals as an alternative to access rules. If a user has an active approval for the repository, the approval overrides access rules until the approval expires. For more details, see How Cyral authorizes a user to connect to a repository.
When multiple database accounts are available for a user
Each access rule maps an SSO user (or group) to a specific database account. If multiple access rules match for an SSO user, that can mean multiple database accounts are available for that SSO user.
If you've set up multiple access rules for an SSO user in this way, then,
when connecting, the user must specify both their SSO username and
their preferred database account name in their connection string.
This usually follows the format, {SSO_USER}:{LOCAL_ACCOUNT}, as explained
in the SSO connection syntax section.
If the the database account name is missing, Cyral denies access because the request is ambiguous.
Access rule expirations and updates
If you or another administrator edits an access rule, or if the access rule expires, this can affect users who are currently connected based on that access rule. In such cases, Cyral performs the access rule evaluation again.
Based on the evaluation, the user's connection may be terminated (because it has become unauthorized) or may continue based on an access rule that applies. Cyral also re-evaluates the Cyral policy that governs the user's data access, so if the newly matched access rule uses a different group name, then the group used for policy evaluation will change.
Add an access rule
Prerequisites
Before you add an access rule, make sure you've completed these steps:
- Set up Cyral to protect your data repository
- If your users connect through SSO, connect Cyral to your SSO identity provider
Procedure
In the Cyral control plane UI, click Data Repos in the left navigation bar, click the name of your repository, and click the User Authentication tab.
Click the name of the database account you will map, or create one now.
Click Add rule.
Choose SSO Group or SSO User to specify the type of SSO identities this rule applies to.
In the text entry field, do one of:
For SSO users: choose Email or User Id and type the corresponding value as stored in your identity provider (IdP).
For SSO groups, type the SSO group name as stored in your IdP.
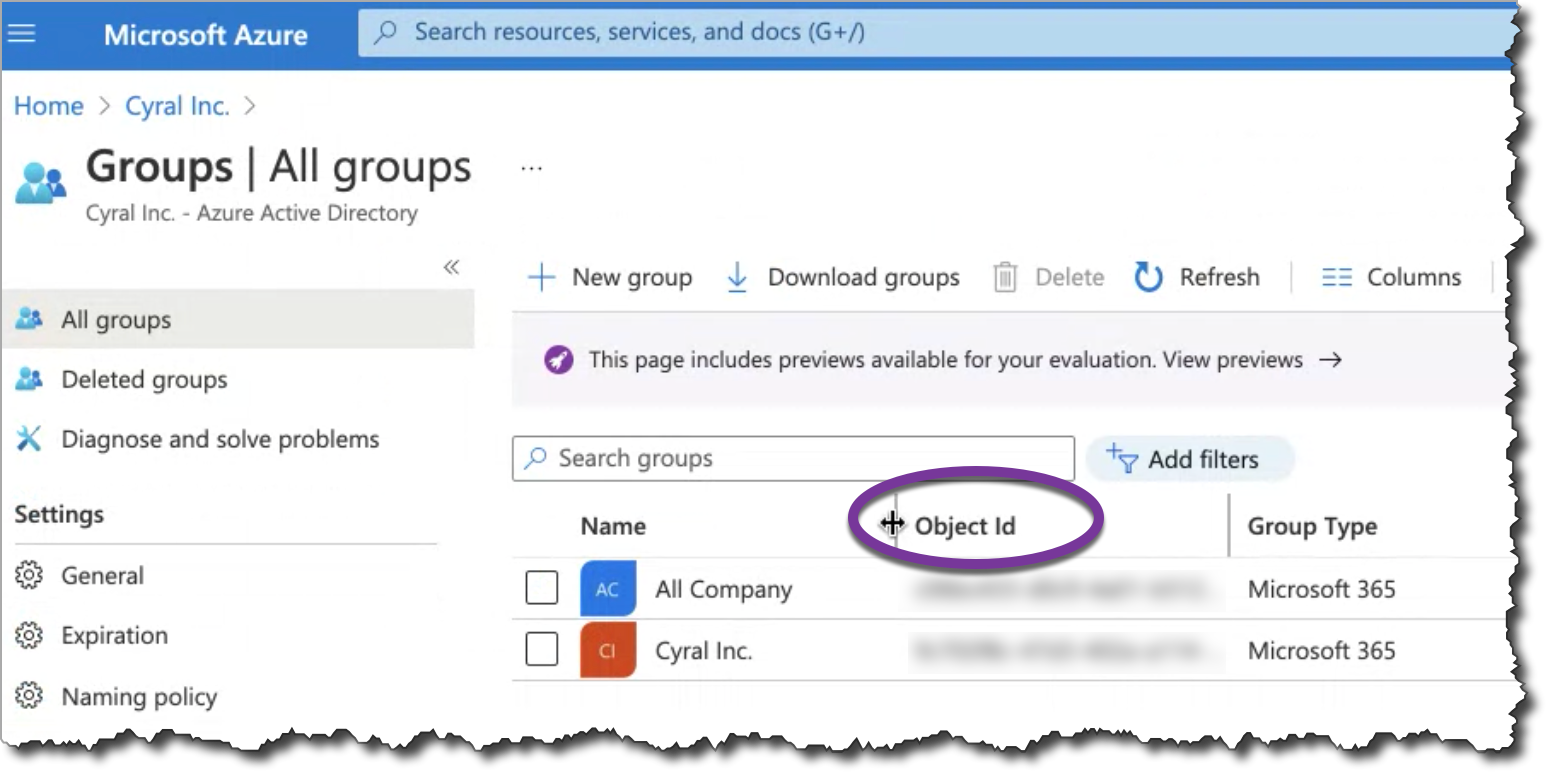
tip
Please note that for Azure AD, you'll specify the SSO group by its Object ID which you'll find in the Groups panel of your Azure management console.
In the When is this access permitted? section, choose one of:
- Always to create a mapping that will not expire automatically; or
- Specify Duration and set a start and end time to set a length of validity for this user's or group's access,
To enforce an on-call access restriction (each user's access grant remains open only during their on-call rotation), follow these steps:
- Open the Additional Access Restrictions section.
- Choose the name of the incident management system integration you saved in Cyral. For setup details, see the incident response system integration instructions.
note
To enforce on-call schedules, you mist set up an on-call schedule in your incident management system, like PagerDuty, and you must connect your incident management system to Cyral
To require multi-factor authentication, follow these steps:
- Open the Additional Access Restrictions section.
- Choose the name of the multifactor-authentication system integration you saved in Cyral. For setup details, see Multi-factor authentication with Duo.
Click Add Rule to save the identity mapping and rule.
With the rule saved, SSO users who match it can connect to the repository using their SSO credentials. To initiate the connection, they must begin at the Cyral Access Portal.
info
As an administrator, you can validate the configuration by creating a local account mapping for yourself, then navigating to your access portal by clicking the Access Tokens button at the top right of your management console.
Next step
- Check that the repository appears in the Cyral Access Portal for the users who need access.
- Follow the instructions in Connect to a data repository with SSO credentials to verify that users can connect based on your new configuration.
tip
Did you know that your users can quickly request and get access to a repository, just by chatting with the Cyral bot in Slack? See how to set it up now.