HashiCorp Vault secrets for database authentication
Cyral supports database account authentication using secrets stored in HashiCorp Vault. This allows you to configure database accounts for your data repositories that are associated with secret paths from your HashiCorp Vault server, and use them for database authentication.
Creating a HashiCorp Vault integration
Navigate to the Integrations page in the sidebar.
Click Setup or Configure on the HashiCorp Vault card, and click the New Integration button.
From there, fill the corresponding fields:
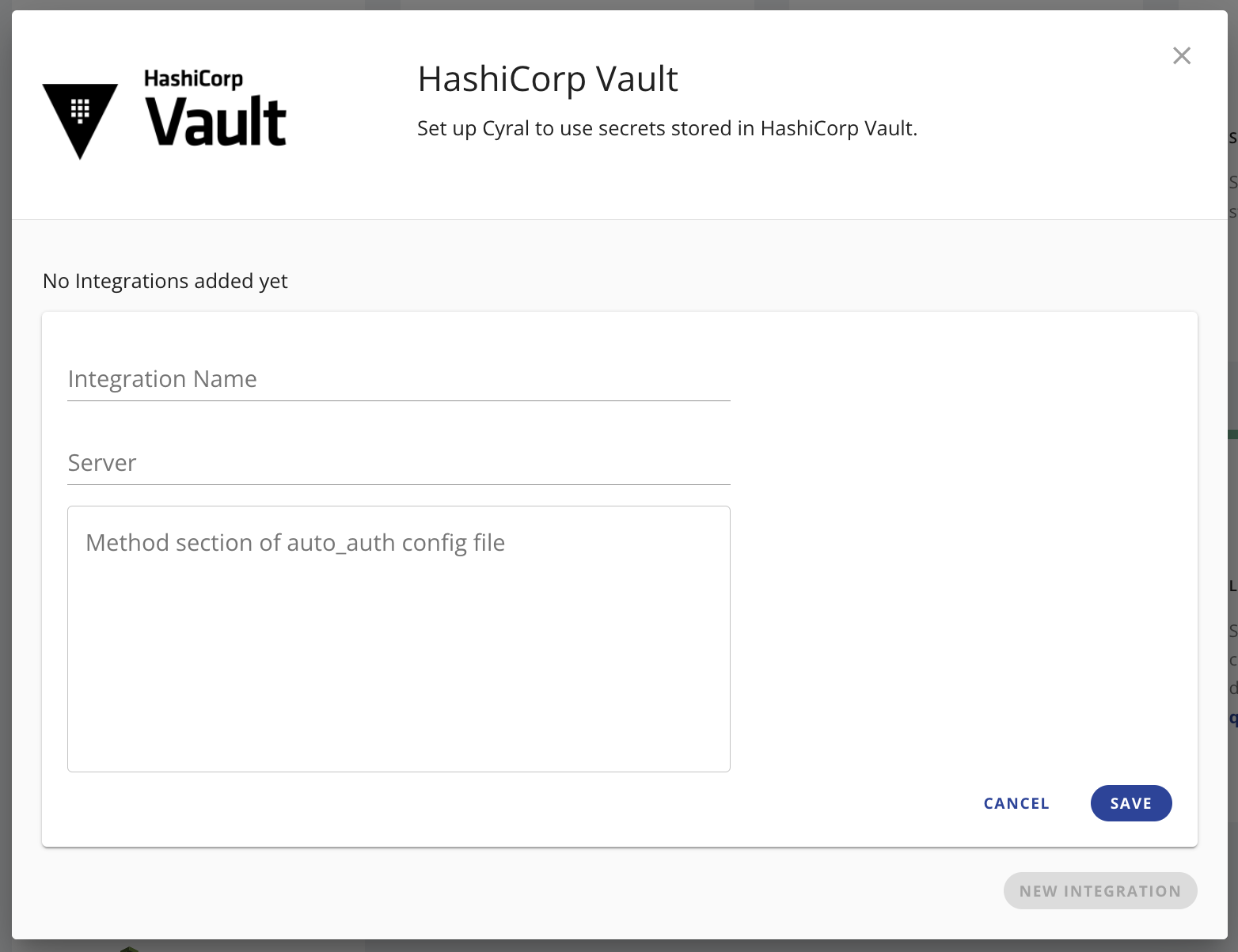
- Integration Name: the name you want to give to this integration.
- Server: the address of the vault server (e.g.
https://vaul-server.com:8200). - Auto-Auth: the Auto-Auth
configuration to be used to automatically manage authentication with the vault server. Here is
an example of an Auto-Auth configuration using the AWS IAM
method:
method "aws" {
mount_path = "auth/aws"
config = {
type = "iam"
role = "cyral_sidecar_role"
region = "us-east-1"
}
}info
If the Auto-Auth field is left empty, the authentication with the vault server must be managed externally by providing a valid token that will be used to authenticate with the vault server, this token can be provided by defining a
VAULT_TOKENenvironment variable at the sidecar container level.
Configuring a Sidecar with a HashiCorp Vault integration
To perform database authentication using the HashiCorp Vault integration you created, the sidecar needs to be configured with the corresponding vault integration.
To do that, from the Cyral control plane UI:
Navigate to the Sidecars page in the sidebar.
Click on the corresponding sidecar you want to configure to use the HashiCorp Vault integration. This will redirect you to the Sidecar Details page.
In the Sidecar Details, go to Settings > Integration Settings and select the corresponding HashiCorp Vault integration that you want the sidecar to use during database authentication.
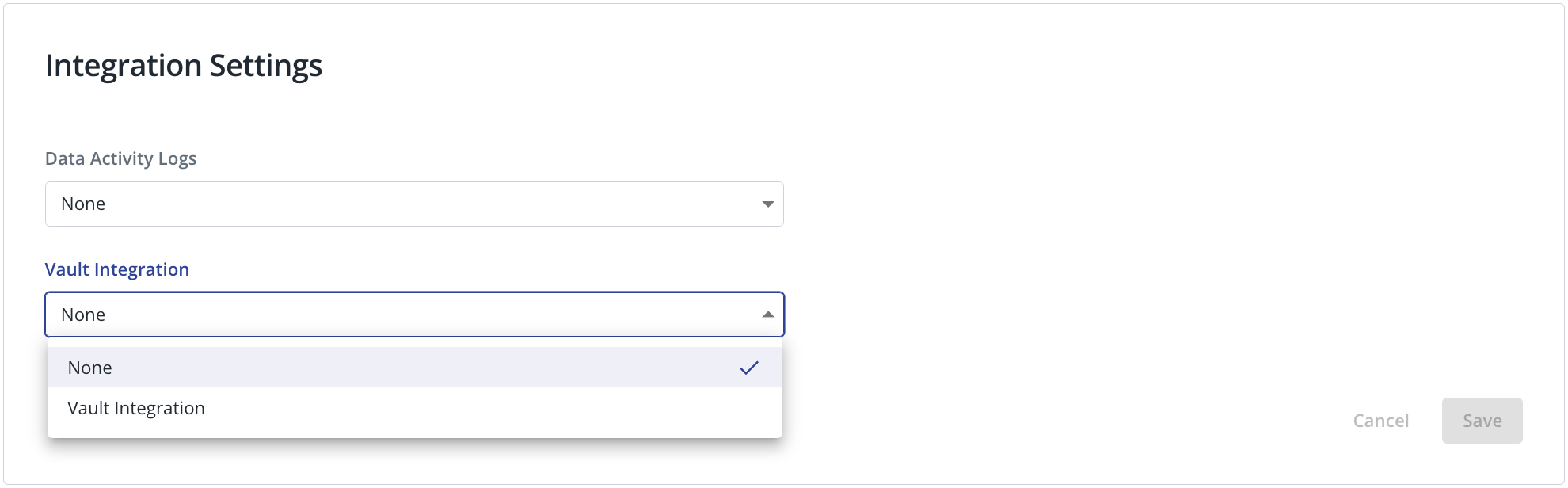
Click on Save to complete the configuration. After that, your sidecar should be ready to use HashiCorp Vault to retrieve database account secrets to authenticate to your data repositories.